A Hilal Computers' SOC-NOC centre in operation
A Hilal Computers' SOC-NOC centre in operation
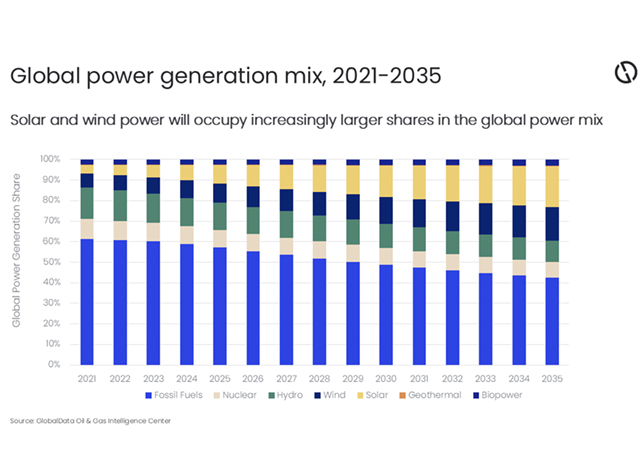
The energy sector comprises thousands of companies responsible for creating, storing, transporting, and distributing energy through a complex network of facilities, pipelines, and power grids.
These enormous networks utilise complex systems and interconnected technologies.
"These essential technologies are increasingly the target of cyberattacks," says Shijas Mohidheen, Director of Cybersecurity of Hilal Computers.
A close analysis of these attacks and breaches underpins the importance of securing the sector’s vast supply chain ecosystem, especially since energy companies acquire hardware and software from third-party vendors that can potentially compromise their security integrity.
"Energy companies face cyber risk from vulnerabilities related to their IT systems, OT infrastructure, and supply chain partners," says Mohidheen.
Supply chain sabotage sometimes occurs unintentionally because of elements in the process that do not meet current security standards, or intentionally as part of a covert effort to facilitate a future attack.
Attacks can come through software updates or ‘patches’, which are downloaded by the company, or through firmware that allow bad actors the opportunity to include malicious codes for exploitation at a later date.
In addition to securing their IT and OT infrastructure, energy companies must also understand their supply chain’s cyber maturity and security processes.
 |
Mohidheen ... cybersecurity focus for energy companies |
"Energy companies should conduct vendor risk assessments and gather ongoing intelligence themselves or through specialised cybersecurity audits and consultancy," says Mohidheen.
To provide customers with the IT and OT expertise needed to manage their own cybersecurity programs or augment their existing teams, Hilal Computers offers OT Security Assessment and Managed Services as part of its industry-leading managed services Secure platform.
The Mission Secure Platform is an all-in-one solution that provides managed visibility for all assets, proactively managed protection, managed analysis and hunting, managed response and support, and additional managed service features and benefits.
These features and services provide customers with a dedicated security engineer for ongoing OT network analysis, threat detection and hunting, redundancy, and secure backend, security information and event management, and secure end-to-end communication.
This platform is built on the best practice principles of a cybersecurity frameworks, namely identify, protect, detect, respond and recover.
"There is always a balance between security and convenience. For energy-related critical infrastructure, the scales should consistently tip toward security, even if at the expense of convenience," concludes Mohidheen.
Hilal Computers is a legally authorised and approved vendor for providing cybersecurity consultancy, governance, and cyber technologies in the Kingdom of Saudi Arabia. It is listed on the website of the National Cybersecurity Authority (NCA) Saudi Arabia.
By Ahmed Suleiman